1. 代理
1.1. ssh
- socks5 走 ssh 隧道实现代理
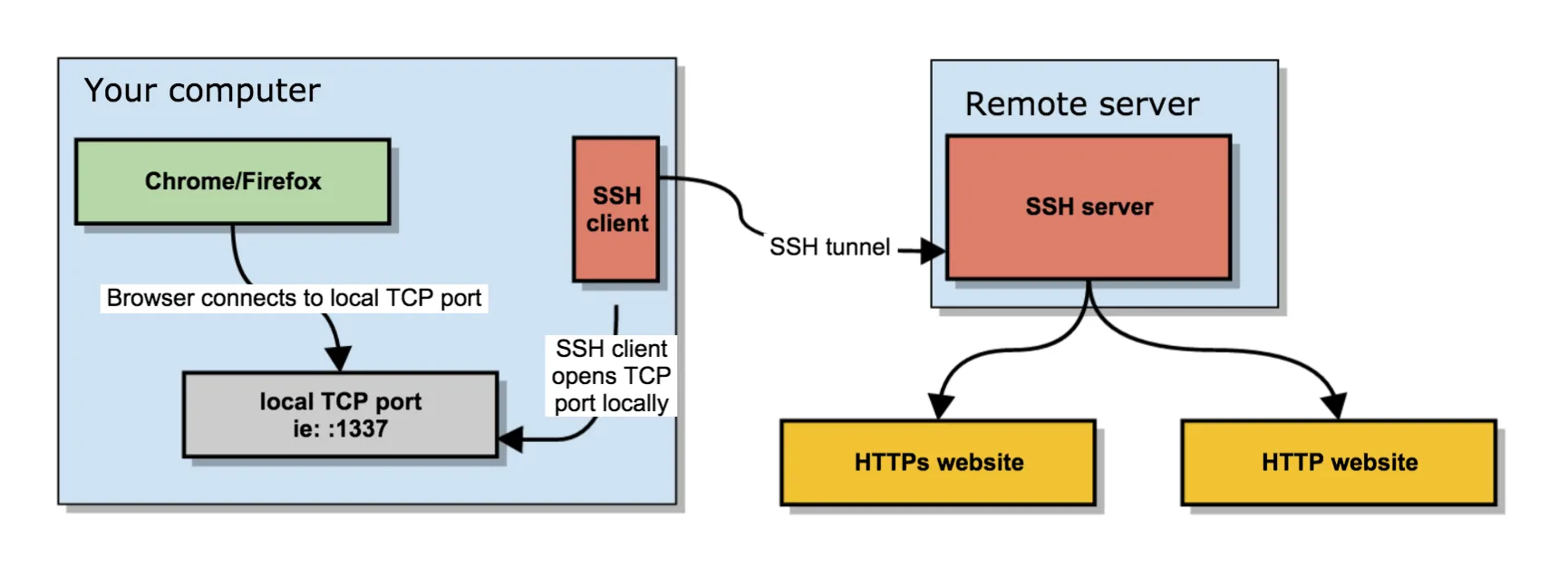
# -D:指定本地监听IP和端口
# -q:静默模式
# -C:压缩节约带宽
# -N:不执行远端命令,仅转发流量
# -f:在后台运行
# user@remote:远程用户@远程主机
ssh -D 0.0.0.0:1337 -q -C -N -f user@remote- 其他
# 本地端口转发 ssh -LNf local-port:target-host:target-port tunnel-host
# -L:转发本地端口。
# -N:不发送任何命令,只用来建立连接。没有这个参数,会在 SSH 服务器打开一个 Shell。
# -f:将 SSH 连接放到后台。没有这个参数,暂时不用 SSH 连接时,终端会失去响应。
ssh -L 3306:192.168.31.194:3306 root@127.0.0.1
# 远程端口转发 ssh -R target-port:local-host:local-port tunnel-host
# -R:转发远程端口。
ssh -R 9999:192.168.2.3:9999 root@1.1.1.1
# 通过~/.ssh/config配置github代理
#Host github.com
# HostName github.com
# ProxyCommand nc -v -X connect -x 127.0.0.1:9999 %h %p2. Android
2.1. adb
adb reboot bootloader # 进入fastboot
adb shell am start -a android.intent.action.VIEW -d scheme:// # 访问指定url
adb shell settings put global http_proxy 127.0.0.1:9999 # 设置代理
adb shell settings put global http_proxy :0 # 取消代理
adb shell setenforce 0 # 关闭SELinux
adb shell setprop persist.device_config.runtime_native.usap_pool_enabled false # 关闭usap
adb shell settings put system screen_off_timeout 100000000 # 设置屏幕常亮
adb shell settings put global ntp_server pool.ntp.org # pixel内置ntp被墙,设置同步时间服务器2.2. fastboot
fastboot reboot # 重启
fastboot boot boot.img # 临时进入boot镜像
fastboot flash boot boot.img # 刷入boot镜像
fastboot -w # 清除userdata,metadata
fastboot update <image.zip> # 刷入zip包2.3. 逆向
- Android Backup 包
java -jar abe.jar unpack cat.ab cat.tar # Android Backup包转换- jadx
jadx-gui --show-bad-codes # jadx无损启动- Xamarin 逆向
import sys, struct, lz4.block, os.path
def main():
if len(sys.argv) != 2:
sys.exit("[i] Usage: " + sys.argv[0] + " in_file.dll")
in_file = sys.argv[1]
with open(in_file, "rb") as compressed_file:
compressed_data = compressed_file.read()
header = compressed_data[:4]
if header != b'XALZ':
sys.exit("[!] Wrong header, aborting...!")
packed_payload_len = compressed_data[8:12]
unpacked_payload_len = struct.unpack('<I', packed_payload_len)[0]
compressed_payload = compressed_data[12:]
decompressed_payload = lz4.block.decompress(compressed_payload, uncompressed_size=unpacked_payload_len)
out_file = in_file.rsplit(".",1)[0] + "_out.dll"
if os.path.isfile(out_file):
sys.exit("[!] Output file [" + out_file + "] already exists, aborting...!")
with open(out_file, "wb") as decompressed_file:
decompressed_file.write(decompressed_payload)
print( "[i] Success!")
print( "[i] File [" + out_file + "] was created as result!")
if __name__ == "__main__":
main()2.4. 系统证书
# 计算证书pem格式的hash,假设输出为9a5ba575
openssl x509 -subject_old_hash -in a.pem
# mac
# openssl x509 -subject_hash_old -in a.pem
# 重命名<hash>.0
mv a.pem 9a5ba575.0Android <= 13
# Create a separate temp directory, to hold the current certificates
# Without this, when we add the mount we can't read the current certs anymore.
mkdir -m 700 /data/local/tmp/htk-ca-copy
# Copy out the existing certificates
cp /system/etc/security/cacerts/* /data/local/tmp/htk-ca-copy/
# Create the in-memory mount on top of the system certs folder
mount -t tmpfs tmpfs /system/etc/security/cacerts
# Copy the existing certs back into the tmpfs mount, so we keep trusting them
mv /data/local/tmp/htk-ca-copy/* /system/etc/security/cacerts/
# Copy our new cert in, so we trust that too
cp /data/local/tmp/9a5ba575.0 /system/etc/security/cacerts/
# Update the perms & selinux context labels, so everything is as readable as before
chown root:root /system/etc/security/cacerts/*
chmod 644 /system/etc/security/cacerts/*
chcon u:object_r:system_file:s0 /system/etc/security/cacerts/*
# Delete the temp cert directory & this script itself
rm -r /data/local/tmp/htk-ca-copyAndroid >= 14,由于安卓14在证书的路径有变化,参考wuxianlin的微博,新路径在/apex/com.android.conscrypt/cacerts,需要增加mount -o bind /system/etc/security/cacerts /apex/com.android.conscrypt/cacerts
或者直接使用现有模块
2.5. pixel刷机
tips:
- 网友建议刷机前四清,防止意外阻止刷机
- 线刷相当于底层替换所有镜像,数据不会保留;卡刷相当于更新系统,数据会保留。(个人理解起名卡刷是因为该模式可以选择
Apply update from SD card) - 降级可以按照线刷的步骤,根据
flash-all脚本,逐步降级
2.5.1. 双清/四清/六清
★★普通双清★★ 普通双清就是在recovery模式下选择:
1:清除数据恢复出厂(wipe data/factory reset) 备注:清除/data(程序数据)和/cache(系统缓存)两个分区(清除用户信息和软件信息),在常用的CWM里(如CWM-based Recovery v6.0.5.0),还包括格式化/sd-ext和/sdcard/.android_secure这两个分区;
2:清除cache分区(wipe cache partition) 说明:仅格式化/cache这一个分区(清除系统缓存),只是用在刷完系统后出现问题,恢复还原用的!
★★四清解释★★ 所谓刷机四清就是在双清的基础上,增加下面两项:
3:Wipe dalvik cache (清除缓存) 说明:高级功能 -> 清除dalvik cache 备注:安卓系统启动时,需要建立一个所有程序的信任分支,以优化缓存文件,以加快启动速度。wipe或者新刷系统后,初次启动很慢,就是因为没有建立这个文件,以后启动就会加快。
4:格式化 / system(格式化系统分区) 说明:挂载和大容量存储 -> 格式化 / system
★★六清解释★★ 所谓刷机六清就是在上面四清的基础上,增加下面两项:
5:格式化 / sdcard(格式化手机内置存储卡) 说明:挂载和大容量存储 -> 格式化 / sdcard
6:格式化 / storage / extsdcard(格式化手机外置TF卡)
2.5.2. 卡刷
- 在
Google页面拉到底部点击Acknowledge出现下载列表,下载对应型号镜像 - 执行
adb reboot recovery进入Recovery模式 - 进入
Recovery模式显示no command后,按住power键然后按一下volume up键进入选项菜单选择Apply update from ADB - 执行
adb sideload <ota file>
2.5.3. 线刷
- 在
Google页面拉到底部点击Acknowledge出现下载列表,下载对应型号镜像 - 使用
unzip解压下载的文件 - 执行
flash-all.sh或flash-all.bat脚本
3. Frida
3.1. 堆栈打印
Java.perform(function () {
var SQLiteDatabase = Java.use("com.tencent.wcdb.database.SQLiteDatabase");
SQLiteDatabase["open"].implementation = function (
bArr,
sQLiteCipherSpec,
i15
) {
console.log(
Java.use("android.util.Log").getStackTraceString(
Java.use("java.lang.Throwable").$new()
)
); //java层打印堆栈
console.log(
"open is called" +
", " +
"bArr: " +
JSON.stringify(bArr) +
", " +
"sQLiteCipherSpec: " +
sQLiteCipherSpec +
", " +
"i15: " +
i15
);
var ret = this.open(bArr, sQLiteCipherSpec, i15);
console.log("open ret value is " + ret);
return ret;
};
});3.2 函数 hook
Java.perform(function () {
var e = Java.use("ir3.e");
e["r"].implementation = function (str, str2, i15, z15) {
console.log(
"r is called" +
", " +
"str: " +
str +
", " +
"str2: " +
str2 +
", " +
"i15: " +
i15 +
", " +
"z15: " +
z15
);
var ret = this.r(str, str2, i15, z15);
console.log("r ret value is " + ret);
return ret;
};
});4. Windows
4.1. hyper-v
Enable-WindowsOptionalFeature -Online -FeatureName Microsoft-Hyper-V -All # 开启hyper-v5. 证书
5.1. openssl
ssh-keygen -y -f ~/.ssh/id_rsa # ssh-keygen导出公钥
openssl x509 -in a.cer -inform der -out a.pem -outform pem # der to pem
# 自签名服务器证书
openssl genrsa -out server.key 2048 # 生成一个私钥文件
openssl req -new -key server.key -out server.csr # 通用名称 (CN)需要填域名*.example.com
openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crt # 生成自签名证书6. Docker
6.1. Docker Desktop version on Mac
# https://stackoverflow.com/questions/64221861/an-error-failed-to-solve-with-frontend-dockerfile-v0
export DOCKER_BUILDKIT=0
export COMPOSE_DOCKER_CLI_BUILD=0
# snap docker 国内源
# /var/snap/docker/current/config/daemon.json
# {
# "log-level": "error",
# "registry-mirrors": [
# "https://docker.mirrors.ustc.edu.cn"
# ]
# }7. Linux
7.1. 扩容
# lvextend -L 10G /dev/mapper/ubuntu--vg-ubuntu--lv //增大或减小至19G
# lvextend -L +10G /dev/mapper/ubuntu--vg-ubuntu--lv //增加10G
# lvreduce -L -10G /dev/mapper/ubuntu--vg-ubuntu--lv //减小10G
# lvresize -l +100%FREE /dev/mapper/ubuntu--vg-ubuntu--lv //按百分比扩
sudo lvresize -l +100%FREE /dev/mapper/ubuntu--vg-ubuntu--lv
# 执行resize2fs使扩容生效
sudo resize2fs /dev/mapper/ubuntu--vg-ubuntu--lv7.2. 自动挂载
crontab -e
# @reboot mount /dev/sdb /home/docker/data7.3. 命令行操作
for i in *; do mv $i ${i}.zip; done # 批量加后缀
for i in *; do mv $i ${i%.*}.zip; done # 批量改后缀
SCRIPT_DIR=$( dirname $(readlink -f $0) ) # 当前目录8. Mysql
# 创建账号及修改账号权限
CREATE DATABASE bizsec CHARACTER SET utf8mb4 COLLATE utf8mb4_general_ci;
CREATE USER 'bizsec'@'%' IDENTIFIED BY 'password';
GRANT ALL PRIVILEGES ON bizsec.* TO 'bizsec'@'%';
FLUSH PRIVILEGES;
SELECT User, Password, Host FROM mysql.user;9. NodeJS
npm config set registry http://mirrors.cloud.tencent.com/npm/ # 配置
npm config get registry # 验证9.1. elecetron 反编译
# https://stackoverflow.com/questions/38523617/how-to-unpack-an-asar-file
npm install -g @electron/asar
npx @electron/asar extract app.asar app # Extract the whole archive:
npx @electron/asar extract-file app.asar main.js #Extract a particular file:10. 编译
clang -o my_program my_program.c -Wl,--verbose # 打印出详细的链接过程,包括使用的库。